SIK-2017-058
Title:
SMS-Tracker Spyware Downloader in Google Play
Report ID
SIK-2017-058
Summary:
- Vendor: Tolencanut Calotenca
- Product: Mobile monitoring – Phone tracker (Package-Name: com.mobmonapp.appd)
- Affected Version: 14.01
- Severity: high
- Short summary: This application is a malware app we found on 2017-08-30. The com.mobonapp.appd is a benign app, but downloads an additional malicious application once opened.
Details:
The original app (package name: com.mobmonapp.appd) contains only two permissions:
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE" />
<uses-permission android:name="android.permission.INTERNET" />
However, on GoolgePlay it promotes its app with:
„Mobile monitoring – Phone tracker“ common features:
- SMS messages tracker – access every message received or sent
- GPS Location tracking – see the location of the cell phone
- Call logs tracker – check incoming and outgoing calls – cell phone tracker of phone calls
- Contacts tracker – the list of contacts should be linked to sms and phone calls.
This is kind of interesting, since the „SMS message tracker“ would need an SMS-read-permission for instance.
After installing the app and opening it for the first time, it shows a screen like this:
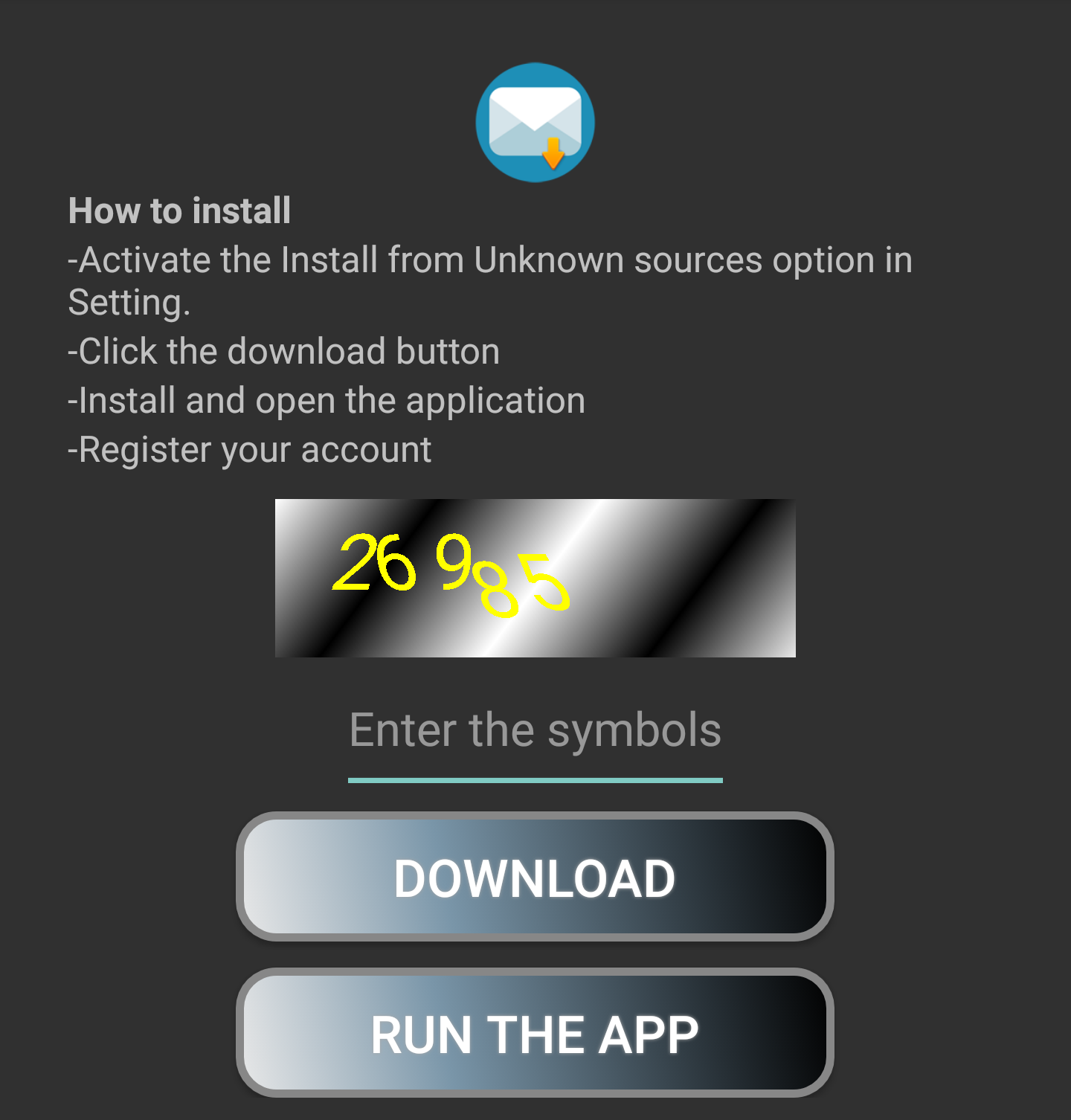
One needs to enter a captcha before you can download the actual malware (com.apps.mondows). The app that gets downloaded contains all the features promoted on the GoolgePlay store. Now, it becomes clear that the app offered on GoolgePlay is just a downloader app. The captcha is probably used to make it a little bit harder for automated dynamic analysis tools that try to click on certain buttons.
The original app tries to hide the download-link in the original app via a simple byte-representation of a string:
$String = staticinvoke AppMain.bytesToAlphabeticString("01101000011101000111010001110000001110100010111100101111011101110111011101110111001011100110011001101100011011110111001001101001011011000110010100101110011100100110111100101111011000010111000001110000001011110110110101101111011011100110010001101111011101110111001100101110011000010111000001101011");
which is actually
$String = http://www.florile.ro/app/mondows.apk
The link points to the actual malware (com.apps.mondows), which gets downloaded. The user has to manually allow third-party installations.
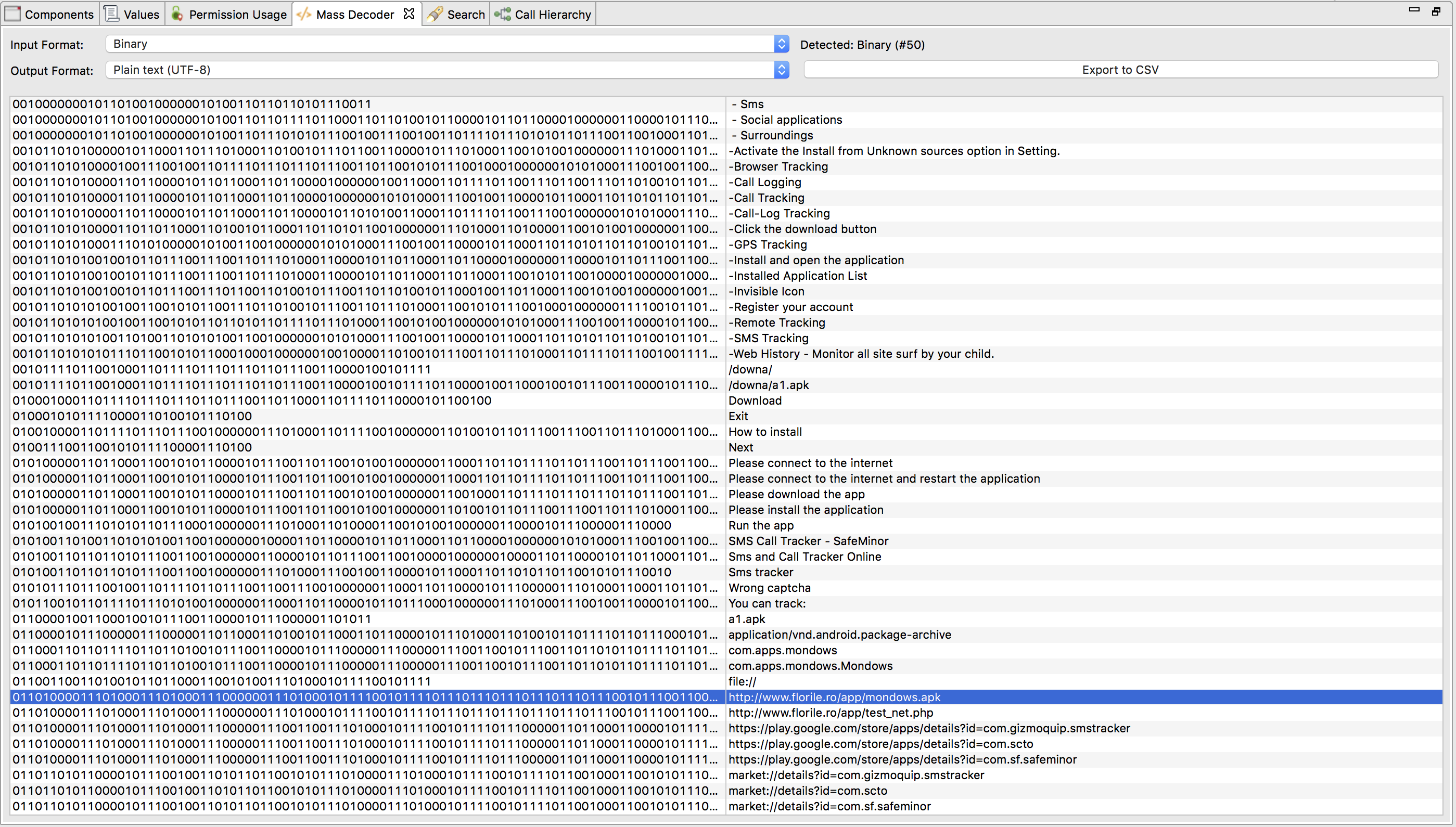
The string-obfuscation trick is used for all strings. With the help of CodeInspect, one is able to display all byte-representation to strings in the „Mass-Decoder“ view:
Workaround
–
Suggested Mitigation
–
Timeline
- 2017-08-30: Malware discovered
- 2017-08-30: Details sent to Android Security Team
- 2017-09-01: Malware removed from Google PlayStore
